Introduction
Using Tines to automate interaction with AWS services requires the use of an AWS credential. When a HTTP Request Action with an AWS mode credential runs, Tines will authorize the request AWS using the Signature Version 4 Signing Process and include the corresponding headers in the request.
Creating an AWS credential
Role-based access
AWS recommends using roles for cross account access - e.g. to allow Tines to access resources in your AWS account. To create a Role-based access AWS credential in Tines, you'll also need to create and correctly configure a Role in your AWS account. The following three steps will get you up and running. For more information, see the AWS tutorial.
Step 1: Create your AWS Credential in Tines
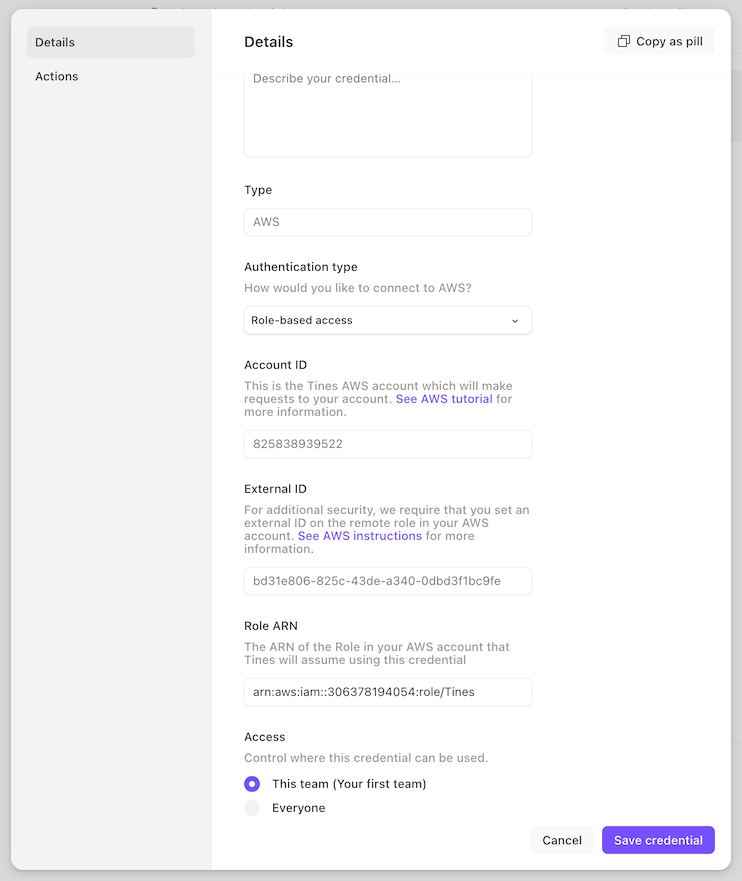
Create a new Credential in Tines. Set the "type" to "AWS", the "Authentication type" to "Role-based access" and enter a name (and, optionally, a description).
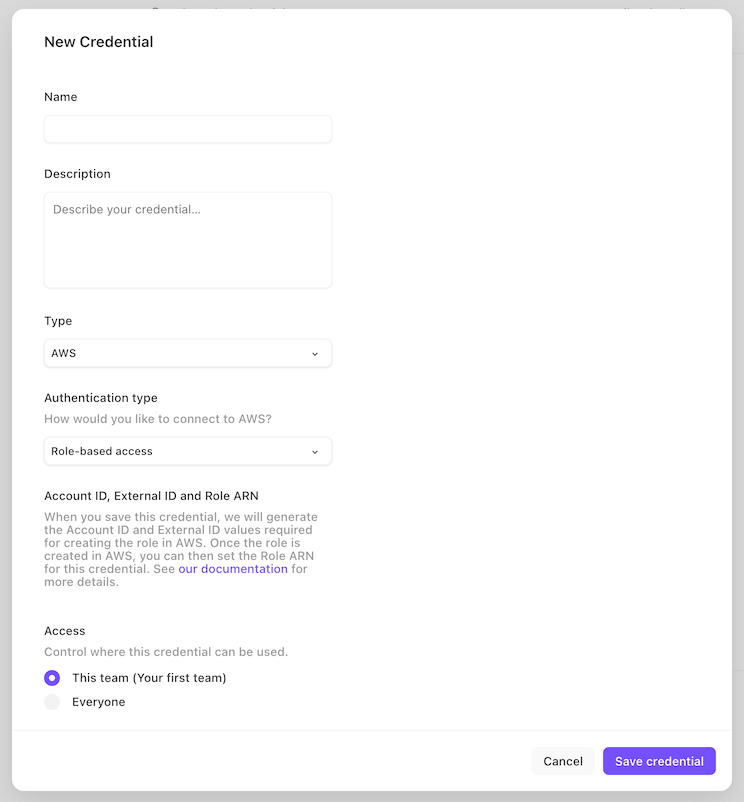
Once you click "Save credential", you'll be presented with an Account ID and External ID:
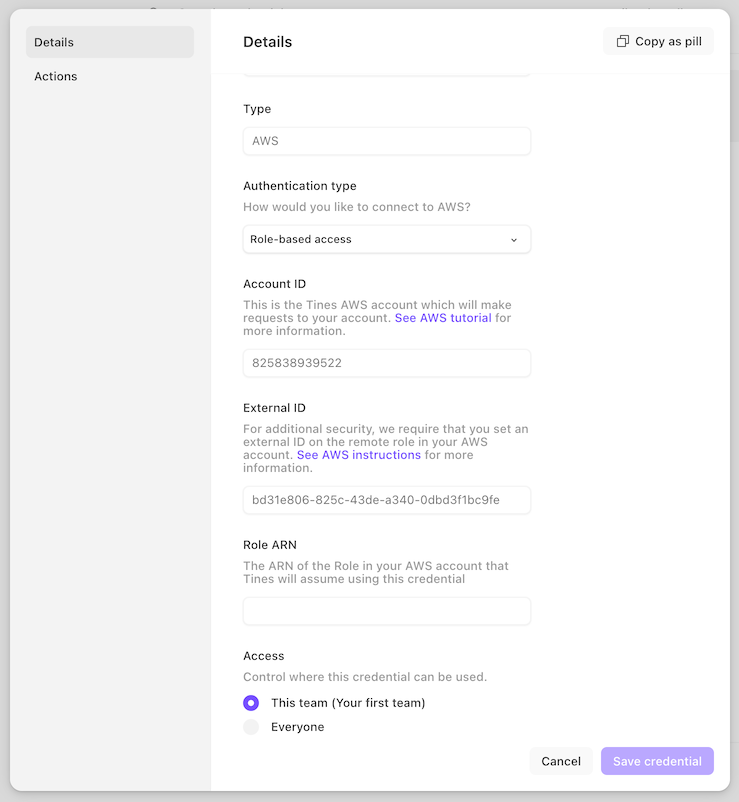
You'll need these values in the next step.
Step 2: Create your Role in AWS
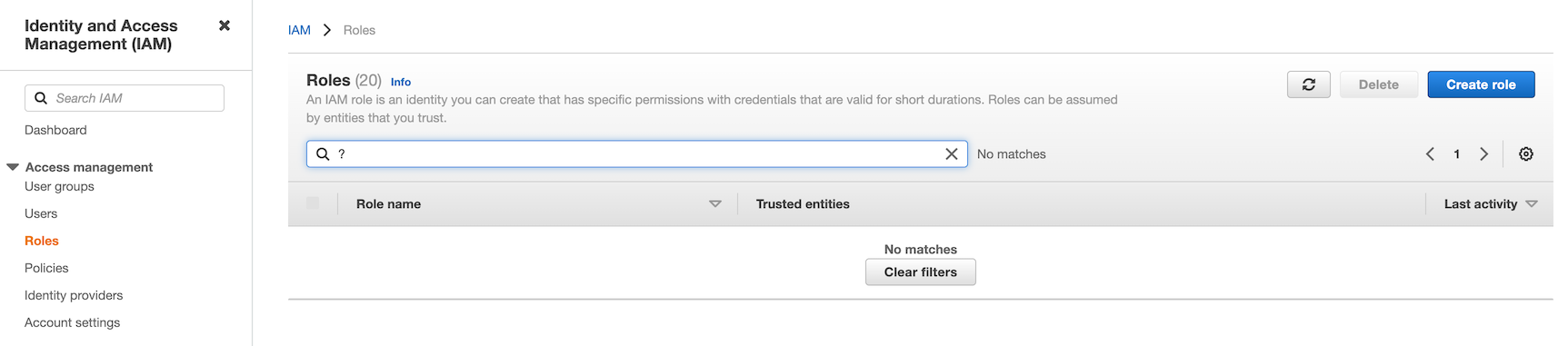
From the Identity and Access Management (IAM) section of the AWS console, navigate to "Roles" and click on "Create role":
For "Trusted entity type", select "AWS account". Select "Another AWS account" and enter the Account ID from step 1. Check "Require external ID" and enter the External ID from step 1.
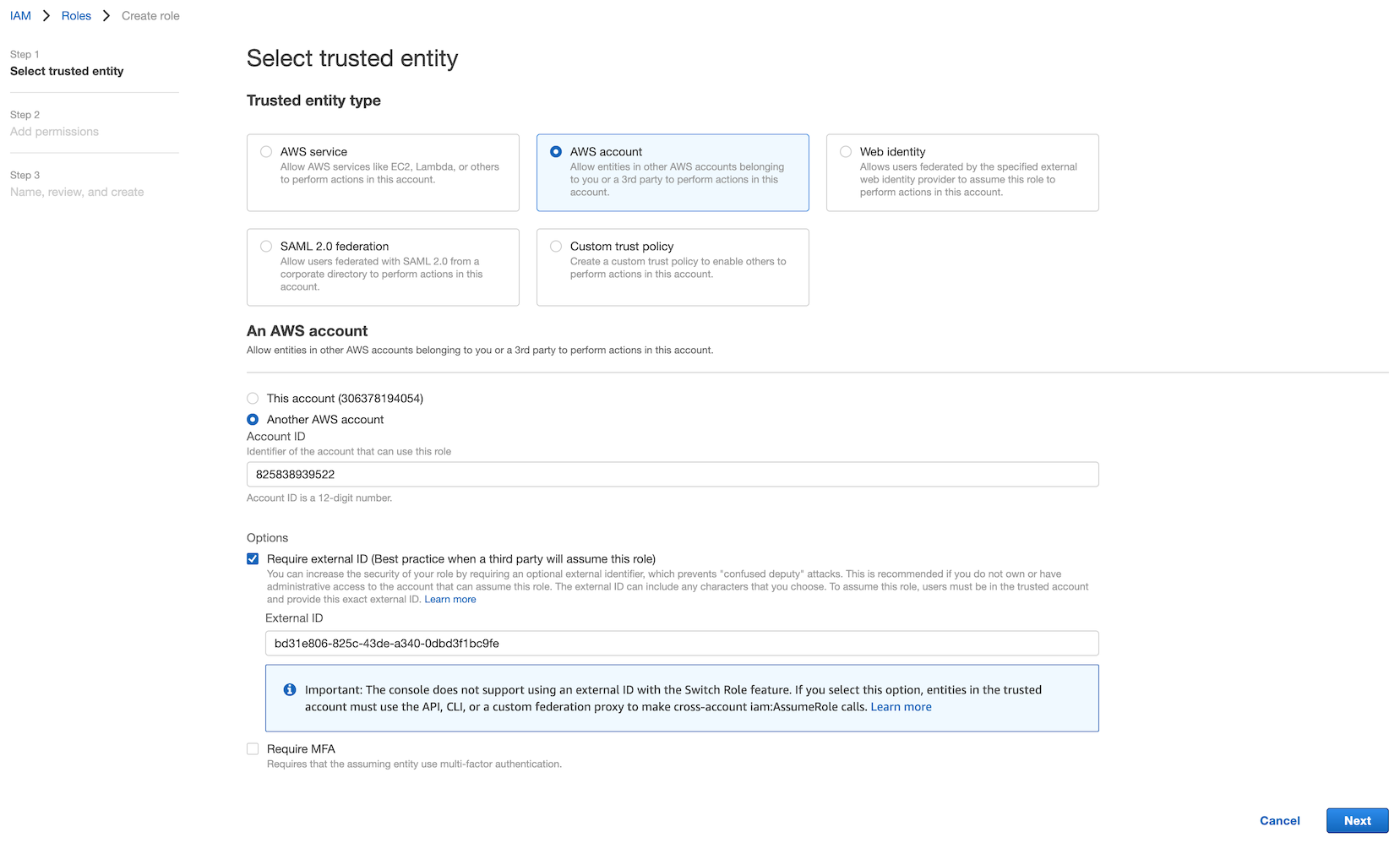
❗️Important
Complete the "Add permissions" and "Name, review and create" steps to finish creating your Role.
Step 3: Add your Role's ARN to your Tines Credential
In the AWS console, open the Role you just created and copy the ARN:
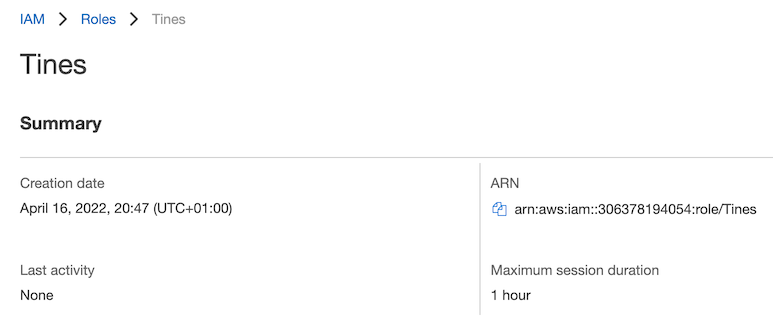
Paste it into the Role ARN field of your Credential in Tines and click "Save credential":
Key-based access
❗️Important
Enter the following information in the AWS New Credential page:
Credential name: Your desired AWS credential name.
Access key: The
access keyfrom your AWS Security Credentials.Access secret: The
access secretfrom your AWS Security Credentials.
If you want to assume a role before performing the action, you can set values for the following fields.
Assumed Role ARN: The ARN of the role you wish to assume, e.g.:
arn:aws:iam::123456789012:role/write-access-role
Tines will request a session with the minimum duration (15 minutes).
Using an AWS credential with a HTTP Request Action
To use an AWS credential with a HTTP Request action, include a CREDENTIAL formula expression in the action's Authorization header.
Sample AWS HTTP Request Actions
Scan a DynamoDB Table
{
"url": "https://dynamodb.eu-west-1.amazonaws.com",
"method": "post",
"content_type": "json",
"payload": {
"TableName": "TestTable",
"AttributesToGet": ["Id"]
},
"headers": {
"Authorization": "<<CREDENTIAL.aws_dynamo_db>>",
"X-Amz-Target": "DynamoDB_20120810.Scan"
}
}List Cloudtrails
{
"url": "https://cloudtrail.us-east-1.amazonaws.com",
"method": "get",
"content_type": "form",
"payload": {
"Action": "DescribeTrails",
"Version": "2013-11-01"
},
"headers": {
"Authorization": "<<CREDENTIAL.aws_cloudtrail>>"
}
}List IAM Users
{
"url": "https://iam.amazonaws.com",
"content_type": "form",
"method": "get",
"payload": {
"Action": "ListUsers",
"Version": "2010-05-08"
},
"headers": {
"Authorization": "<<CREDENTIAL.aws_iam>>"
}
}